Press release
New Endpoint Protector 4 – Device Control Hardware and Virtual Appliance: Faster, Stronger, Adaptable Data and Device Security for Businesses
Endpoint Protector 4, the data loss prevention, device control and endpoint security solution for Windows and Mac OS starts shipping todayBucharest, October 27, 2011. In September 2011 alone, over 20 million private records worldwide have been exposed in security breaches, affecting businesses around the world. To prevent such incidents, endpoint security developer CoSoSys has released a new version of their flagship device control and data loss prevention solution, Endpoint Protector. Offering enhanced protection, increased effectiveness and the fastest implementation time in its segment, the out-of-the-box Hardware and Virtual Appliance is now available for small, medium and large companies and organizations.
The new version ensures complete control over the latest portable and mobile devices available as well as full support and protection for the latest Windows operating systems and Mac OS X versions, including Mac OS X Lion. By continuously adapting to new and highly spread security threats affecting both small businesses and large corporations, Endpoint Protector 4 focuses not only on proactively protecting company networks from data loss, leakage and theft by blocking, controlling and monitoring all ports, but also on offering complete detailed reports on the information transferred in and out of the network.
“With Endpoint Protector 4 we stay true to our goal of protecting companies of all sizes and complexity levels from all the threats posed in the modern business environment,” said Roman Foeckl, CoSoSys CEO. “We make sure we offer optimum data and port control security so that companies are able to benefit from new technologies that come with instant connectivity, high mobility, large storage capacities and successfully integrate them in their existing business workflow.”
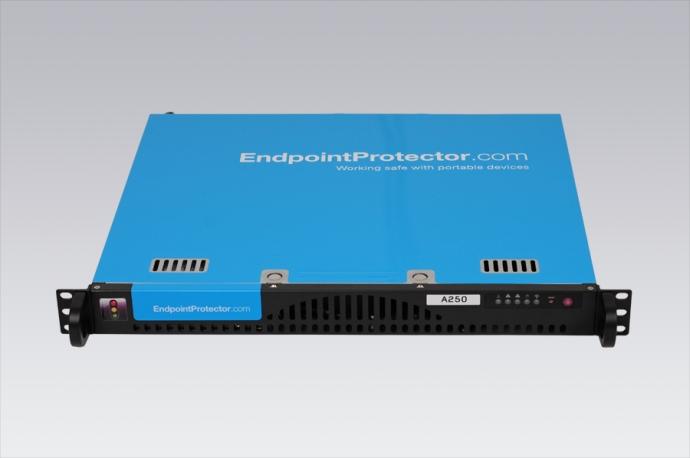
Endpoint Protector 4, available as both virtual and Hardware Appliance, is designed to minimize internal threats, reduce data leakage risks and control devices connected at Windows and Macintosh endpoints. It allows IT departments to proactively take control of the devices’ internal use, while tracking all data transferred in or out of the protected network and enforcing encryption of data in transit on portable devices.
The Endpoint Protector 4 Hardware Appliance is offered for a network with 50 Endpoints at 1.199,- Euros. Other models of the Hardware Appliance for smaller or larger networks are available ranging from protecting 20 endpoints to more than 5.000 endpoints.
For more details on the Endpoint Protector 4 Hardware and Virtual Appliance, visit:
http://www.endpointprotector.com/en/index.php/products/endpoint_protector_appliance
Some of the new features in Endpoint Protector 4 are detailed below:
• Seamless integration in business processes – Endpoint Protector 4 provides high adaptability to an organization’s structure (from 20 up to 5.000 computers), allowing separate control and dedicated policies for each segment. Each organizational unit’s activity is closely monitored by a different administrator, shielding it from the interference of other departments and keeping data access and knowledge limited to unit employees.
• Saving time and money when the solution is installed - Reduce staff efforts required by the now easier to perform download, installation, and registration processes, including a new licensing system.
• Increased security through enhanced protection – Enforced encryption of data transferred to devices now through EasyLock 2 and TrustedDevices, security passwords for sensitive data report access, prevention against removal and security alerts setting.
• Reducing allotted resources of the security staff – Easy maintenance on the Server side through the new Live Update module, client deployment through latest Microsoft Active Directory versions and client software upgrades by a simple push of a button.
• Optimum security through enhanced stability – Better client-server communication, streamlined updates and maintenance, fast client deployment and installation.
• Enhanced protection through complex, adaptable end efficient security policies - Custom protected device categories (iPhone, iPad, iPod Touch, etc.), more control over policies management and more options for log file management.
• Reliable security through enhanced monitoring and policy control - Enhanced monitoring of device use, real time and offline tracing of encrypted and non-encrypted data and instant shadow copying of transferred files with EasyLock 2.
Images and additional materials:
http://www.cososys.com/press_room.html
Press Contacts:
Mirror Communications
Alina Popescu
Phone: +40 741 073753
E-mail: alina@mirror-communications.com
CoSoSys Ltd.
Anca Goron
Phone: +40 264 593 110 Ext. 113
E-mail: anca.goron@cososys.com
About CoSoSys
CoSoSys is specialized in network device control, endpoint security and data loss prevention (DLP) for Windows / Mac and development of applications for portable storage device enhancement. The application portfolio includes functions from device control, file tracing and shadowing, password security, data synchronization and network security. CoSoSys distributes its products globally through Distributors, Resellers and directly to users at http://www.EndpointProtector.com and http://www.CoSoSys.com. CoSoSys is an independent software developer since a management buyout from Astaro in July 2011. CoSoSys enjoys a continuously growing installation base of users worldwide and was recognized in 2011 as one of the fastest growing technology companies being a winner of the 2011 Deloitte Technology FAST 50 ranking for Central Europe. The company has offices in Germany, the United States and Romania.
CoSoSys Ltd.
Haiducului 6
400040 Cluj-Napoca
Romania
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release New Endpoint Protector 4 – Device Control Hardware and Virtual Appliance: Faster, Stronger, Adaptable Data and Device Security for Businesses here
News-ID: 198084 • Views: …
More Releases from CoSoSys Ltd.

Endpoint Protector 4 named Best DLP Solution Finalist in the SC Awards Europe 20 …
Our Data Loss Prevention Solution Endpoint Protector 4 has made the shortlist in the Best DLP Solution category
Cluj-Napoca, Romania, February 18th, 2013. With competitive companies entering and strict judging criteria, SC Awards Europe honors the most innovative security technologies. CoSoSys announces proudly that Endpoint Protector 4, its Data Loss Prevention, Device Control and Mobile Device Management solution has been named Finalist in the run for the selection of the Best…

Thunderbolt and USB 3.0 ports: two more reasons for companies to use Device Cont …
Support for Thunderbolt and USB 3.0 ports against data theft and data leakage through portable storage devices is essential to protect company data is now available with Endpoint Protector 4 for Mac OS X
Cluj-Napoca, Romania, January 24th, 2013. While the number of companies incorporating more and more Macs into their networks is increasing, the need for protecting these computers against data leakage and data theft is rising. Especially since all…

Endpoint Protector, Winner in the 2012 Mobile Star Awards™
Endpoint Protector named “Superstar” for the category Enterprise Solutions: Security and “Shining Star” for Enterprise Solutions: Mobile Device Management category in the 2012 Mobile Star Awards™!
Bucharest, Romania, December 20, 2012. CoSoSys is proud to announce that its innovative Data Loss Prevention, Device Control and Mobile Device Management solution, Endpoint Protector, has been named winner in the 11th Annual Mobile Star Awards™ program, organized by the mobile technology news and events…
More Releases for Endpoint
Unified Endpoint Management Market: Unified Endpoint Management to Surge to USD …
Unified Endpoint Management Market Scope:
Key Insights : Unified Endpoint Management Market size was valued at USD 6.36 Billion in 2022 and is poised to grow from USD 8.41 Billion in 2023 to USD 78.43 billion by 2031, at a CAGR of 32.2% during the forecast period (2024-2031).
Discover Your Competitive Edge with a Free Sample Report :https://www.skyquestt.com/sample-request/unified-endpoint-management-market
Access the full 2024 Market report for a comprehensive understanding @https://www.skyquestt.com/report/unified-endpoint-management-market
In-Depth Exploration of the…
Endpoint Security Management Market: Ready To Fly on high Growth Trends | Avast, …
The Latest published market study on Endpoint Security Management Market provides an overview of the current market dynamics in the Endpoint Security Management space, as well as what our survey respondents- all outsourcing decision-makers- predict the market will look like in 2029. The study breaks the market by revenue and volume (wherever applicable) and price history to estimate the size and trend analysis and identify gaps and opportunities. Some of…
Revving Up Security: Automotive Endpoint Authentication
An endpoint authentication mechanism is used to verify/track the identity of external devices connected to a network, thereby ensuring the connectivity of only authorized endpoint devices. An endpoint authentication is of vital importance for networks that have flurry of remote users. The mechanism is also implemented via an endpoint authentication system, which not only verifies users but also monitors incoming connections of endpoint devices. At present, cars are equipped with…
Endpoint Security Market - Need to Prevent Cyber Attacks and Threats Driving Dem …
In a recent report by Transparency Market Research (TMR), the global endpoint security market is expected to witness an intense competitive environment as the vendor landscape of the market is highly fragmented. This is because of the presence of a number of vendors on the basis of small-scale, regional, and also large multi-national scale basis. Owing to the intense environment of competition in the market, all players focus on making…
Endpoint Security Management Market 2018: Emerging Industries, Size, Share, Chal …
Endpoint Security Management Market Research Report 2018 gives estimation of the factors that are boosting the development of the Endpoint Security Management market size, share, growth prospects, segments, future trends, and industry outlook, development status. The report on global endpoint security management market identifies key attributes about the customer to define the potential market and identify different needs across the industry.
Get Sample Copy of this Report -https://www.orianresearch.com/request-sample/558686
Market Overview: The…
Endpoint Detection and Response Market Analytical Tools are used to Identify the …
The EDR market is broadly segmented on the basis of deployment type, organization size, industry vertical and geography. On the basis of deployment type, global EDR market is segmented into on premise, managed services or hybrid deployment.
On the basis of organization size, global EDR market is classified into small & medium sized enterprises (SMEs) and large enterprises.
Furthermore, the major industry verticals that are benefitted by EDR solutions include…